We Help You Fortify Your Defences: Robust Cybersecurity Solutions
Safeguard your business against digital threats with our comprehensive cybersecurity expertise.



Service Overview
Newmeric Global FZCO provides a comprehensive suite of cybersecurity services to protect your organization from evolving threats. We help you build a robust security posture to safeguard your data, systems, and reputation.
Key Features & Benefits:
- Threat Detection and Prevention
- Data Protection
- Advanced Firewall and Network Security
- Identity and Access Management (IAM)
- Incident Response and Recovery
- Compliance and Regulatory Adherence
- Employee Training and Awareness
Service Offerings
Threat Detection & Response
- Intrusion Detection and Prevention Systems (IDPS)
- Security Information and Event Management (SIEM)
- Threat Intelligence & Hunting
- Incident Response Planning & Execution
Security Audits & Assessments
- Vulnerability Assessments & Penetration Testing
- Compliance Audits (e.g., SOC 2, ISO 27001)
Security Architecture & Design
- Security Information and Event Management (SIEM) implementation
- Cloud Security Architecture
- Identity and Access Management (IAM) solutions
Security Awareness Training
- Employee cybersecurity training programs
- Phishing simulations and awareness campaigns
Methodology/ Approach
Risk Assessment & Prioritization
We conduct thorough risk assessments to identify and prioritize your most critical security needs.
Layered Security Approach
We implement a layered approach to security, combining preventative, detective, and responsive measures.
Continuous Security Support
We provide ongoing monitoring, maintenance, and support to ensure your security posture remains strong.
Flow chart
Cybersecurity Lifecycle
Identify

Protect

Detect

Respond

Recover

|
Factors
|
Newmeric Global FZCO
|
Traditional Approach
|
|---|---|---|
|
Focus
|
Proactive threat prevention and response
|
Reactive measures, limited threat intelligence
|
|
Technology
|
Leverage of advanced security technologies, AI/ML
|
Reliance on outdated technologies, limited threat detection capabilities
|
|
Expertise
|
Deep expertise in cybersecurity best practices and emerging threats
|
Limited security expertise, potential for gaps in coverage
|
|
Visibility
|
Enhanced visibility into security threats and vulnerabilities
|
Limited visibility into security threats and potential blind spots
|
|
Response
|
Rapid response to security incidents, minimizing impact
|
Slow response times, increased risk of data loss
|
|
Compliance
|
Ensure compliance with industry regulations and data privacy standards
|
Potential for non-compliance with regulations
|
|
Client Relationship
|
Close client collaboration, dedicated security consultants
|
Limited client involvement, lack of ongoing support
|
Partner with Us for Innovative Tech Solutions!
At Newmeric Global FZCO, we believe in building lasting partnerships that drive success through cutting-edge technology.
Whether you’re looking to enhance your website, streamline operations, or innovate your business processes, we’re here to help.
Partner with us and take your digital transformation to the next level!
Frequently Asked Questions
Here are some common questions we receive about our Cyber Security service

Common threats include ransomware, phishing attacks, malware, data breaches, and denial-of-service attacks.
Regular security assessments, such as penetration testing and vulnerability scans, should be conducted on an ongoing basis, typically at least annually.
Regular employee training programs, phishing simulations, and awareness campaigns are crucial to educate employees about cybersecurity threats and best practices.
Threat detection involves identifying and monitoring potential threats. Threat response involves taking immediate action to contain and mitigate the impact of a security incident.
Key metrics include the number of security incidents, mean time to detection and response, and the number of vulnerabilities identified and remediated.
Maximize Your Wealth with Our Cutting-Edge Financial Solutions


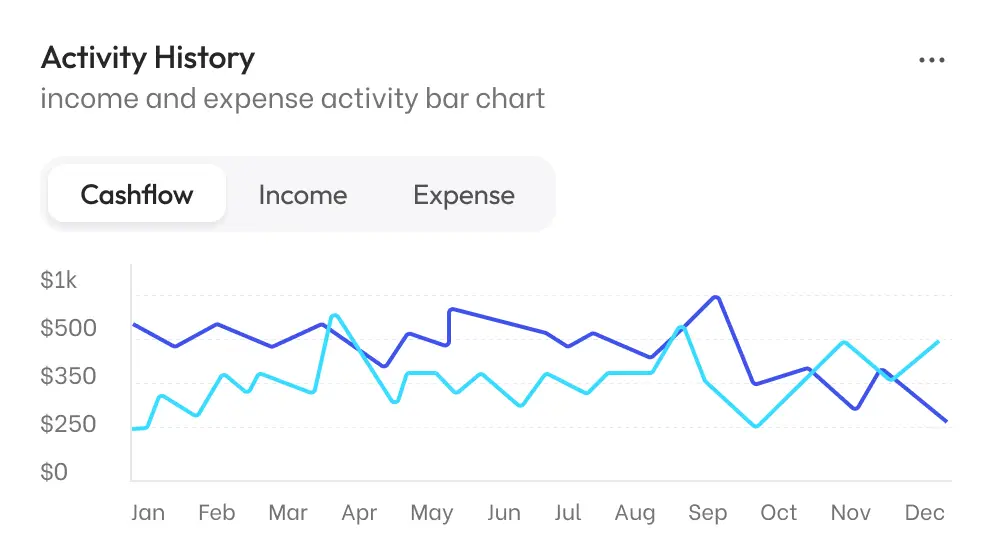
Comprehensive Solutions
Commitment to Excellence
We’re committed to providing you with the highest level of service and excellence. Our financial solutions are designed to help you achieve your financial objectives.
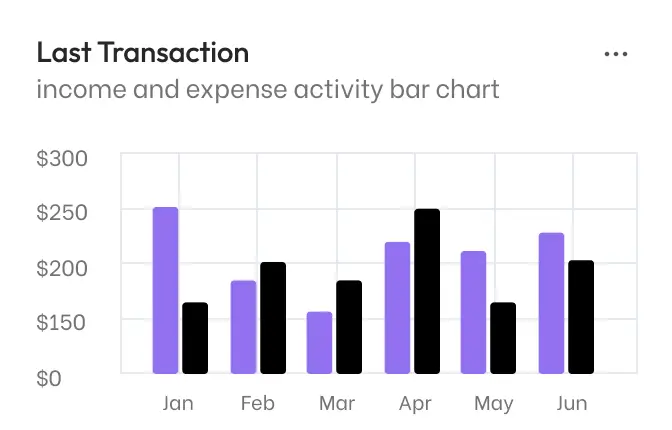
Expert Financial Solutions
What Our Clients Say

Paityn Dorwart

Jaydon Bator

James Mango

Corey Korsgaard

Aspen George
